Brutalmethode gewählt:
Von https://packages.debian.org/sid/all/ca-certificates-java/download das Paket geholt, dann
me@xubuntu:/tmp$ sudo apt install ./ca-certificates-java_20240118_all.deb
[sudo] Passwort für me:
Paketlisten werden gelesen… Fertig
Abhängigkeitsbaum wird aufgebaut… Fertig
Statusinformationen werden eingelesen… Fertig
Hinweis: »ca-certificates-java« wird an Stelle von »./ca-certificates-java_20240118_all.deb« gewählt.
Die folgenden Pakete werden aktualisiert (Upgrade):
ca-certificates-java
1 aktualisiert, 0 neu installiert, 0 zu entfernen und 0 nicht aktualisiert.
Es müssen noch 0 B von 11,6 kB an Archiven heruntergeladen werden.
Nach dieser Operation werden 0 B Plattenplatz zusätzlich benutzt.
Holen:1 /tmp/ca-certificates-java_20240118_all.deb ca-certificates-java all 20240118 [11,6 kB]
(Lese Datenbank ... 358749 Dateien und Verzeichnisse sind derzeit installiert.)
Vorbereitung zum Entpacken von .../ca-certificates-java_20240118_all.deb ...
Entpacken von ca-certificates-java (20240118) über (20190909ubuntu1.2) ...
ca-certificates-java (20240118) wird eingerichtet ...
Neue Version der Konfigurationsdatei /etc/ca-certificates/update.d/jks-keystore wird installiert ...
Warning:
<debian:ubuntuone-valicert_class_2_va.pem> verwendet 1024-Bit-RSA-Schlüssel. Dies gilt als Sicherheitsrisiko. Diese Schlüsselgröße wird in einem zukünftigen Upda
te deaktiviert.
Replacing debian:ACCVRAIZ1.pem
Replacing debian:AC_RAIZ_FNMT-RCM.pem
Adding debian:AC_RAIZ_FNMT-RCM_SERVIDORES_SEGUROS.pem
Replacing debian:Actalis_Authentication_Root_CA.pem
Replacing debian:AffirmTrust_Commercial.pem
Replacing debian:AffirmTrust_Networking.pem
Replacing debian:AffirmTrust_Premium_ECC.pem
Replacing debian:AffirmTrust_Premium.pem
Replacing debian:Amazon_Root_CA_1.pem
Replacing debian:Amazon_Root_CA_2.pem
Replacing debian:Amazon_Root_CA_3.pem
Replacing debian:Amazon_Root_CA_4.pem
Adding debian:ANF_Secure_Server_Root_CA.pem
Replacing debian:Atos_TrustedRoot_2011.pem
Adding debian:Atos_TrustedRoot_Root_CA_ECC_TLS_2021.pem
Adding debian:Atos_TrustedRoot_Root_CA_RSA_TLS_2021.pem
Replacing debian:Autoridad_de_Certificacion_Firmaprofesional_CIF_A62634068.pem
Replacing debian:Baltimore_CyberTrust_Root.pem
Adding debian:BJCA_Global_Root_CA1.pem
Adding debian:BJCA_Global_Root_CA2.pem
Replacing debian:Buypass_Class_2_Root_CA.pem
Replacing debian:Buypass_Class_3_Root_CA.pem
Replacing debian:CA_Disig_Root_R2.pem
Adding debian:Certainly_Root_E1.pem
Adding debian:Certainly_Root_R1.pem
Replacing debian:Certigna.pem
Adding debian:Certigna_Root_CA.pem
Adding debian:certSIGN_Root_CA_G2.pem
Replacing debian:certSIGN_ROOT_CA.pem
Adding debian:Certum_EC-384_CA.pem
Replacing debian:Certum_Trusted_Network_CA_2.pem
Replacing debian:Certum_Trusted_Network_CA.pem
Adding debian:Certum_Trusted_Root_CA.pem
Replacing debian:CFCA_EV_ROOT.pem
Adding debian:CommScope_Public_Trust_ECC_Root-01.pem
Adding debian:CommScope_Public_Trust_ECC_Root-02.pem
Adding debian:CommScope_Public_Trust_RSA_Root-01.pem
Adding debian:CommScope_Public_Trust_RSA_Root-02.pem
Replacing debian:Comodo_AAA_Services_root.pem
Replacing debian:COMODO_Certification_Authority.pem
Replacing debian:COMODO_ECC_Certification_Authority.pem
Replacing debian:COMODO_RSA_Certification_Authority.pem
Replacing debian:DigiCert_Assured_ID_Root_CA.pem
Replacing debian:DigiCert_Assured_ID_Root_G2.pem
Replacing debian:DigiCert_Assured_ID_Root_G3.pem
Replacing debian:DigiCert_Global_Root_CA.pem
Replacing debian:DigiCert_Global_Root_G2.pem
Replacing debian:DigiCert_Global_Root_G3.pem
Replacing debian:DigiCert_High_Assurance_EV_Root_CA.pem
Adding debian:DigiCert_TLS_ECC_P384_Root_G5.pem
Adding debian:DigiCert_TLS_RSA4096_Root_G5.pem
Replacing debian:DigiCert_Trusted_Root_G4.pem
Adding debian:D-TRUST_BR_Root_CA_1_2020.pem
Adding debian:D-TRUST_EV_Root_CA_1_2020.pem
Replacing debian:D-TRUST_Root_Class_3_CA_2_2009.pem
Replacing debian:D-TRUST_Root_Class_3_CA_2_EV_2009.pem
Adding debian:emSign_ECC_Root_CA_-_C3.pem
Adding debian:emSign_ECC_Root_CA_-_G3.pem
Adding debian:emSign_Root_CA_-_C1.pem
Adding debian:emSign_Root_CA_-_G1.pem
Replacing debian:Entrust.net_Premium_2048_Secure_Server_CA.pem
Replacing debian:Entrust_Root_Certification_Authority_-_EC1.pem
Replacing debian:Entrust_Root_Certification_Authority_-_G2.pem
Adding debian:Entrust_Root_Certification_Authority_-_G4.pem
Replacing debian:Entrust_Root_Certification_Authority.pem
Replacing debian:ePKI_Root_Certification_Authority.pem
Adding debian:e-Szigno_Root_CA_2017.pem
Adding debian:GDCA_TrustAUTH_R5_ROOT.pem
Replacing debian:GlobalSign_ECC_Root_CA_-_R4.pem
Replacing debian:GlobalSign_ECC_Root_CA_-_R5.pem
Replacing debian:GlobalSign_Root_CA.pem
Replacing debian:GlobalSign_Root_CA_-_R3.pem
Adding debian:GlobalSign_Root_CA_-_R6.pem
Adding debian:GlobalSign_Root_E46.pem
Adding debian:GlobalSign_Root_R46.pem
Adding debian:GLOBALTRUST_2020.pem
Replacing debian:Go_Daddy_Class_2_CA.pem
Replacing debian:Go_Daddy_Root_Certificate_Authority_-_G2.pem
Adding debian:GTS_Root_R1.pem
Adding debian:GTS_Root_R2.pem
Adding debian:GTS_Root_R3.pem
Adding debian:GTS_Root_R4.pem
Adding debian:HARICA_TLS_ECC_Root_CA_2021.pem
Adding debian:HARICA_TLS_RSA_Root_CA_2021.pem
Replacing debian:Hellenic_Academic_and_Research_Institutions_ECC_RootCA_2015.pem
Replacing debian:Hellenic_Academic_and_Research_Institutions_RootCA_2015.pem
Adding debian:HiPKI_Root_CA_-_G1.pem
Adding debian:Hongkong_Post_Root_CA_3.pem
Replacing debian:IdenTrust_Commercial_Root_CA_1.pem
Replacing debian:IdenTrust_Public_Sector_Root_CA_1.pem
Replacing debian:ISRG_Root_X1.pem
Adding debian:ISRG_Root_X2.pem
Replacing debian:Izenpe.com.pem
Replacing debian:Microsec_e-Szigno_Root_CA_2009.pem
Adding debian:Microsoft_ECC_Root_Certificate_Authority_2017.pem
Adding debian:Microsoft_RSA_Root_Certificate_Authority_2017.pem
Adding debian:NAVER_Global_Root_Certification_Authority.pem
Replacing debian:NetLock_Arany_=Class_Gold=_Főtanúsítvány.pem
Replacing debian:OISTE_WISeKey_Global_Root_GB_CA.pem
Adding debian:OISTE_WISeKey_Global_Root_GC_CA.pem
Replacing debian:QuoVadis_Root_CA_1_G3.pem
Replacing debian:QuoVadis_Root_CA_2_G3.pem
Replacing debian:QuoVadis_Root_CA_2.pem
Replacing debian:QuoVadis_Root_CA_3_G3.pem
Replacing debian:QuoVadis_Root_CA_3.pem
Adding debian:Sectigo_Public_Server_Authentication_Root_E46.pem
Adding debian:Sectigo_Public_Server_Authentication_Root_R46.pem
Replacing debian:Secure_Global_CA.pem
Replacing debian:SecureSign_RootCA11.pem
Replacing debian:SecureTrust_CA.pem
Adding debian:Security_Communication_ECC_RootCA1.pem
Replacing debian:Security_Communication_RootCA2.pem
Adding debian:Security_Communication_RootCA3.pem
Replacing debian:Security_Communication_Root_CA.pem
Adding debian:SSL.com_EV_Root_Certification_Authority_ECC.pem
Adding debian:SSL.com_EV_Root_Certification_Authority_RSA_R2.pem
Adding debian:SSL.com_Root_Certification_Authority_ECC.pem
Adding debian:SSL.com_Root_Certification_Authority_RSA.pem
Adding debian:SSL.com_TLS_ECC_Root_CA_2022.pem
Adding debian:SSL.com_TLS_RSA_Root_CA_2022.pem
Replacing debian:Starfield_Class_2_CA.pem
Replacing debian:Starfield_Root_Certificate_Authority_-_G2.pem
Replacing debian:Starfield_Services_Root_Certificate_Authority_-_G2.pem
Replacing debian:SwissSign_Gold_CA_-_G2.pem
Replacing debian:SwissSign_Silver_CA_-_G2.pem
Replacing debian:SZAFIR_ROOT_CA2.pem
Adding debian:Telia_Root_CA_v2.pem
Replacing debian:TeliaSonera_Root_CA_v1.pem
Adding debian:TrustAsia_Global_Root_CA_G3.pem
Adding debian:TrustAsia_Global_Root_CA_G4.pem
Adding debian:Trustwave_Global_Certification_Authority.pem
Adding debian:Trustwave_Global_ECC_P256_Certification_Authority.pem
Adding debian:Trustwave_Global_ECC_P384_Certification_Authority.pem
Replacing debian:T-TeleSec_GlobalRoot_Class_2.pem
Replacing debian:T-TeleSec_GlobalRoot_Class_3.pem
Replacing debian:TUBITAK_Kamu_SM_SSL_Kok_Sertifikasi_-_Surum_1.pem
Adding debian:TunTrust_Root_CA.pem
Replacing debian:TWCA_Global_Root_CA.pem
Replacing debian:TWCA_Root_Certification_Authority.pem
Adding debian:UCA_Extended_Validation_Root.pem
Adding debian:UCA_Global_G2_Root.pem
Replacing debian:USERTrust_ECC_Certification_Authority.pem
Replacing debian:USERTrust_RSA_Certification_Authority.pem
Adding debian:vTrus_ECC_Root_CA.pem
Adding debian:vTrus_Root_CA.pem
Replacing debian:XRamp_Global_CA_Root.pem
done.
Trigger für ca-certificates (20240203~22.04.1) werden verarbeitet ...
Updating certificates in /etc/ssl/certs...
0 added, 0 removed; done.
Running hooks in /etc/ca-certificates/update.d...
Updating Mono key store
Mono Certificate Store Sync - version 6.8.0.105
Populate Mono certificate store from a concatenated list of certificates.
Copyright 2002, 2003 Motus Technologies. Copyright 2004-2008 Novell. BSD licensed.
Importing into legacy system store:
I already trust 166, your new list has 146
12 previously trusted certificates were removed.
Certificate removed: C=NL, O=Staat der Nederlanden, CN=Staat der Nederlanden EV Root CA
Certificate removed: C=US, O=Google Trust Services LLC, CN=GTS Root R1
Certificate removed: C=TR, L=Ankara, O=E-Tuğra EBG Bilişim Teknolojileri ve Hizmetleri A.Ş., OU=E-Tugra Sertifikasyon Merkezi, CN=E-Tugra Certification Authority
Certificate removed: C=US, O=Network Solutions L.L.C., CN=Network Solutions Certificate Authority
Certificate removed: C=HK, O=Hongkong Post, CN=Hongkong Post Root CA 1
Certificate removed: O="Cybertrust, Inc", CN=Cybertrust Global Root
Certificate removed: C=TR, L=Ankara, O=E-Tugra EBG A.S., OU=E-Tugra Trust Center, CN=E-Tugra Global Root CA RSA v3
Certificate removed: C=US, O=Google Trust Services LLC, CN=GTS Root R2
Certificate removed: C=ES, O=Agencia Catalana de Certificacio (NIF Q-0801176-I), OU=Serveis Publics de Certificacio, OU=Vegeu https://www.catcert.net/verarrel (c
)03, OU=Jerarquia Entitats de Certificacio Catalanes, CN=EC-ACC
Certificate removed: OU=GlobalSign Root CA - R2, O=GlobalSign, CN=GlobalSign
Certificate removed: C=ES, CN=Autoridad de Certificacion Firmaprofesional CIF A62634068
Certificate removed: C=GR, O=Hellenic Academic and Research Institutions Cert. Authority, CN=Hellenic Academic and Research Institutions RootCA 2011
Import process completed.
Importing into BTLS system store:
I already trust 154, your new list has 146
Certificate added: C=ES, CN=Autoridad de Certificacion Firmaprofesional CIF A62634068
Certificate added: C=US, O=Google Trust Services LLC, CN=GTS Root R1
Certificate added: C=US, O=Google Trust Services LLC, CN=GTS Root R2
3 new root certificates were added to your trust store.
12 previously trusted certificates were removed.
Certificate removed: C=HK, O=Hongkong Post, CN=Hongkong Post Root CA 1
Certificate removed: C=GR, O=Hellenic Academic and Research Institutions Cert. Authority, CN=Hellenic Academic and Research Institutions RootCA 2011
Certificate removed: C=US, O=Google Trust Services LLC, CN=GTS Root R2
Certificate removed: OU=GlobalSign Root CA - R2, O=GlobalSign, CN=GlobalSign
Certificate removed: C=TR, L=Ankara, O=E-Tuğra EBG Bilişim Teknolojileri ve Hizmetleri A.Ş., OU=E-Tugra Sertifikasyon Merkezi, CN=E-Tugra Certification Authority
Certificate removed: C=ES, O=Agencia Catalana de Certificacio (NIF Q-0801176-I), OU=Serveis Publics de Certificacio, OU=Vegeu https://www.catcert.net/verarrel (c
)03, OU=Jerarquia Entitats de Certificacio Catalanes, CN=EC-ACC
Certificate removed: C=TR, L=Ankara, O=E-Tugra EBG A.S., OU=E-Tugra Trust Center, CN=E-Tugra Global Root CA RSA v3
Certificate removed: C=ES, CN=Autoridad de Certificacion Firmaprofesional CIF A62634068
Certificate removed: C=US, O=Google Trust Services LLC, CN=GTS Root R1
Certificate removed: C=NL, O=Staat der Nederlanden, CN=Staat der Nederlanden EV Root CA
Certificate removed: O="Cybertrust, Inc", CN=Cybertrust Global Root
Certificate removed: C=US, O=Network Solutions L.L.C., CN=Network Solutions Certificate Authority
Import process completed.
Done
done.
Trigger für ca-certificates-java (20240118) werden verarbeitet ...
done.
Nochmal geguckt
me@xubuntu:~/Dokumente/edfg/pp_prog_0.74.0$ dpkg -l | grep ca-cert
ii ca-certificates 20240203~22.04.1 all Common CA certificates
ii ca-certificates-java 20240118 all Common CA certificates (JKS keystore)
ii ca-certificates-mono 6.8.0.105+dfsg-3.2 all Common CA certificates (Mono keystore)
Sieht gut aus.
Nochmal
me@xubuntu:~/Dokumente/edfg/pp_prog_0.74.0$ ./PortfolioPerformance 2> stderr.txt
Und siehe da:
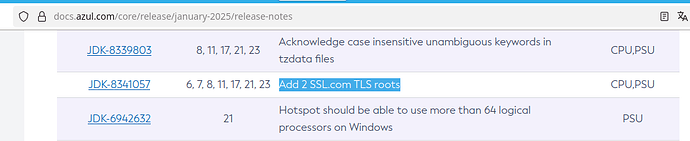
javax.net.ssl|DEBUG|C2|Worker-0: Wechselkurse von Europäische Zentralbank aktualisieren|2025-03-09 15:28:11.794 CET|X509TrustManagerImpl.java:246|Found trusted certificate (
"certificate" : {
"version" : "v3",
"serial number" : "14:03:f5:ab:fb:37:8b:17:40:5b:e2:43:b2:a5:d1:c4",
"signature algorithm": "SHA384withECDSA",
"issuer" : "CN=SSL.com TLS ECC Root CA 2022, O=SSL Corporation, C=US",
"not before" : "2022-08-25 18:33:48.000 CEST",
"not after" : "2046-08-19 18:33:47.000 CEST",
"subject" : "CN=SSL.com TLS ECC Root CA 2022, O=SSL Corporation, C=US",
"subject public key" : "EC",
"extensions" : [
{
ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 89 8F 2F A3 E8 2B A0 14 54 7B F3 56 B8 26 5F 67 ../..+..T..V.&_g
0010: 38 0B 9C D0 8...
]
]
},
Keine Fehler mehr, hurra.
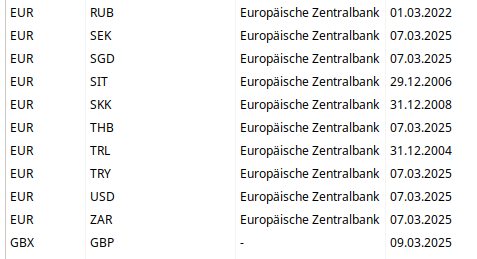
Und z.B. USD mit Datum 07.03.2025